Don't trust comments
And habitually review the third party code you're using - even when it's in the standard library.
NimForum
NimForum is a project by Nim language developers that demonstrates both the front and back end capabilities of the Nim language. It's a standard forum-like web application for different communities - people can post threads and reply to them.
I was recently playing around with it and testing its capabilities. What caught my eye is that NimForum enables formatting with reStructuredText instead of other commonly used dialects such as Markdown or BBCode. RST is far more powerful than the latter options and exposes various directives which the author of a document can use.
One of these directives is include, which allows including files in the generated output. As the documentation states, this is a dangerous directive and introduces an obvious security hole when left enabled.
Nim's standard library
NimForum uses the rstToHtml procedure from the docutils/rstgen package in the standard library in order to do most of the heavy lifting of converting RST-formatted text to HTML. The procedure's docstring states the following:
The proc is meant to be used in online environments without access to a meaningful filesystem, and therefore rst
includelike directives won't work.
In addition, the myFindFile procedure is passed to the include directive handler:
proc myFindFile(filename: string): string =
# we don't find any files in online mode:
result = ""
All of this leads to believe that include directives flat out won't work. However, this is not the case.
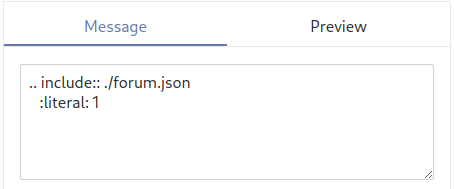
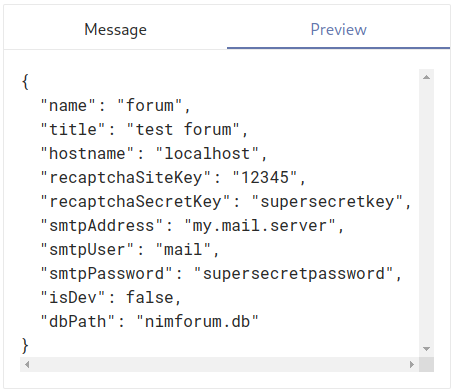
We included ./forum.json and the contents of the forum's configuration file (with secrets) are printed when the /preview endpoint is used. This also works with absolute file paths, such as /etc/passwd. This issue is quite serious and was given the CVE ID CVE-2022-23602. The vulnerability itself affected all NimForum instances, including the one hosted at forum.nim-lang.org.
Hidden functionality
Even if you go through all of RST's documentation and disable all unsafe directives such as include, csv, and so on that allow including local files, it turns out that Nim's rstgen package has extended the code-block directive to also include files using the file field. Even if you were extremely familiar with reStructuredText and all of its unsafe directives, this would probably slip by unnoticed if nobody reviewed code.
Mitigation
If you're using NimForum for your community, you should upgrade to version 2.2.0 ASAP. The security advisory for NimForum can be found here.
The issue in the Nim standard library has been fixed by commit cb894c70, which introduces additional by-default sandboxing. This sandboxing can be disabled with the roSandboxDisabled flag if desirable.
Timeline
- 28/01/2022 - Nim core maintainer notified
- 28/01/2022 - Maintainer confirmation
- 28/01/2022 - Private security advisory created
- 29/01/2022 - Fix pushed to Nim upstream
- 29/01/2022 - CVE requested
- 29/01/2022 - Security advisory published
- 31/01/2022 - CVE ID assigned
- 31/01/2022 - This article published