ksoft's Easy Auto Refresh extension is selling your data
I was doing some work with Burp Suite through Chrome (which I don't often do) and very soon I realised that all of my requests were being relayed to a domain edatasales.com. After probing around a bit, I narrowed it down to the Easy Auto Refresh plugin for Chrome, which currently has over half a million downloads. Disabling this plugin also stopped all requests to edatasales.com.
A sample request looks something like this:
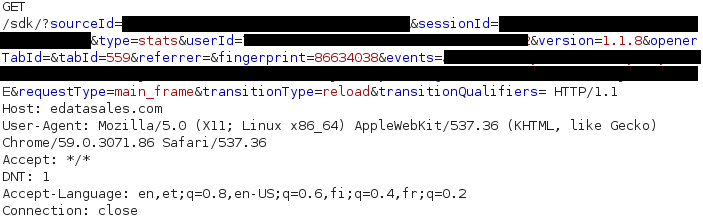
It includes a number of things, an important one being the events parameter. This parameter is simply a base64 encoded string containing, amongst other things, the URL you visited and your device's location.
Every single URL, its referrer, how you got to that site, your location, etc. are being sent to some server hosted using DigitalOcean, which is what the domain edatasales.com resolves to.
The last part of the extension's description on its Chrome web store page mentions this:
By installing this add-on, you agree to the following terms of use http://www.dummysoftware.com/easy-auto-refresh.html#terms
The terms themselves are as follows:
By installing the free version of Easy Auto Refresh you agree to the following terms of use (not applicable in the registered version): You acknowledge and agree that we may use anonymous data capture, syndication analysis and other similar tools to track, extract, compile, aggregate and analyze any data or information resulting from your use of the add-on and that we may share or make available this information with our business partners. All captured data is anonymous and contains no personally identifiable information. If you object to any of these uses, you may uninstall the add-on from your browser.
However, the information being sent is hardly anonymous, and the data is being sent from all visited pages - the extension doesn't have to be in use, just enabled in the extensions menu. I imagine most people install this extension for a one-time use and then forget about it, just as I did.
NOTE: Other plugins offered by this dev are New Tab Changer and Email Exporter. I have not tested whether these extensions also harvest your data, but personally, I wouldn't use these extensions either.
I did report this on the Chrome web store, however, knowing how slow Google is to handle reports it might be weeks until this is addressed. Here's to hoping that's not the case.
This does make one wonder about the current state of the Chrome web store and other Google-run app stores. The Play store comes in mind, as there have been reports of malicious apps being on the store for weeks after being reported. Google needs to step up their game before they are starting to be seen as untrustworthy.
EDIT: Looks like this has been discovered before, 2 months ago. The fact that this has still not been removed from the store, and that the extension still tracks your data, is troublesome.